在上一篇的系列活動中,我們跟各位介紹了什麼是Anthos Bare Metal,以及在部署前,應該要先搜集哪些資訊、如何進行規劃、設置deploy config file,當這一切都就緒完畢後,只需要可以透過bmctl的指令工具,就可以將我們的環境,透過自動化的腳本完成部署,進入K8S的世界來進行探索!
如果您有在關注Anthos發展,您可能會問我說,奇怪,我印象中在Anthos bare metal推出前,應該還有一個GKE On-Prem(現在稱之為Anthos on VMware)的版本不是嗎?為何小編卻先是介紹Anthos Bare Metal呢? 其實這是有原因的,因為大部分的客戶,在接觸K8S時,大多是先從開源版本開始入門的,所以小編希望讓各位能夠循序漸進地了解,在Google推出整合版本後的變化、差異,因此才會優先跟各位介紹Anthos on Bare Metal,接著才介紹今天的主角,在正式進入主題前,我們再幫各位複習一下,讓各位能夠快速的回顧一下兩者之間的差異、優劣。
Anthos 支援多元方式部署,客戶可依據IT環境現況、需求,自由選擇雲端、地端(虛擬化/實體機)的部署模式
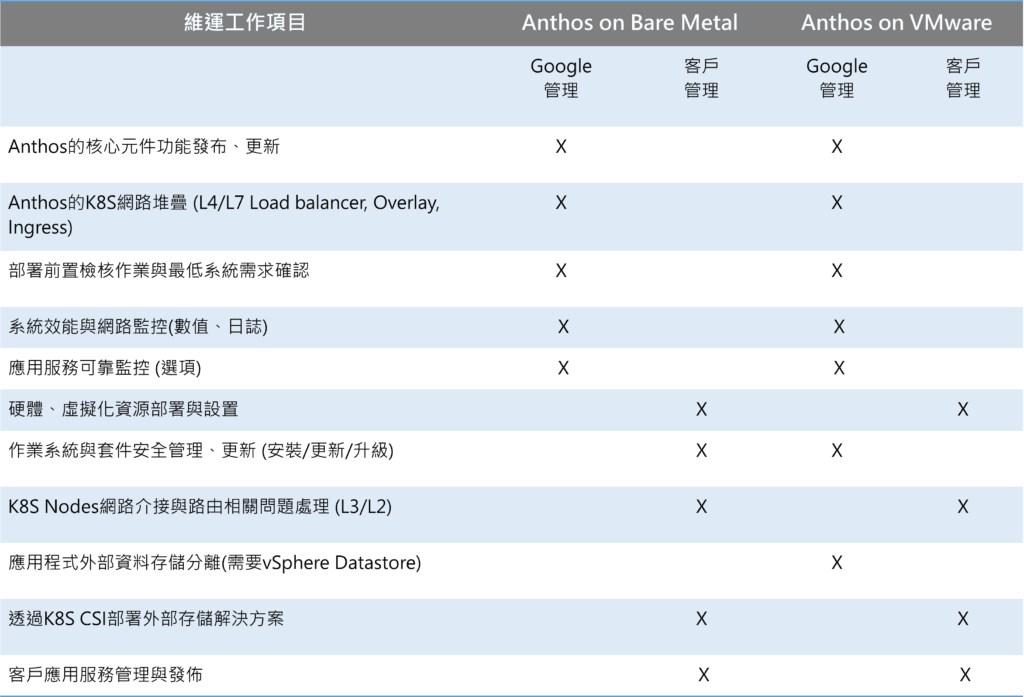
如果Anthos on Bare Metal是倚天劍的話,那麼Anthos on VMware就是當之無愧的屠龍刀了,它是一個與VMWare高度整合的K8S方案,部署的方式跟Anthos on Bare Metal極為相似,用的是gkectl的指令工具,一樣是要預先準備好部署設定檔,接下自動化工具就會把一切都打理好!
Anthos on VMware 藉由與VMware的高度整合,大幅度的簡化客戶環境的K8S日常維運管理,例如:系統升級、資源擴增/縮減、數據存儲、自動修復等…
但,就只是更進階的部署工具而已嗎?如果只是這樣,那也太坑爹了吧!當您選擇了Anthos on VMware的方案後,你就可以獲得近似雲上的GKE叢集的自動部署、自動修復、擴展等功能,不像Anthos on Bare Metal,您需要自行處理K8S master/worker系統的更新與升級、手動配置。
Anthos on VMware採用的是全自動的方式,針對K8S的更新、升級,是透過直接下載雲上驗證過的K8S image,搭配VMware平台的API進行自動化(更新/擴增/刪減)的部署,除此之外,也透過VMware平台的優勢,幫助客戶一次性的解決數據存儲的問題,像是FC / iSCSI / NFS / vSAN等常見的存儲型態,通通都支援,在Anthos on VMware部署的過程中,就可以一次搞定,未來要微調,也可以直接透過VMware平台進行處理,不用再大動干戈的針對K8S進行全面性的重新調整,萬一搞壞了,還真不知道該如何處理、復原呢?!不是嗎?
說了這麼多,是不是迫不及待了呢!那實際部署起來,到底是如何呢?就讓我們帶各位一起瞧瞧吧!
Anthos 提供自動化部署工具,幫助管理者快速佈建叢集環境
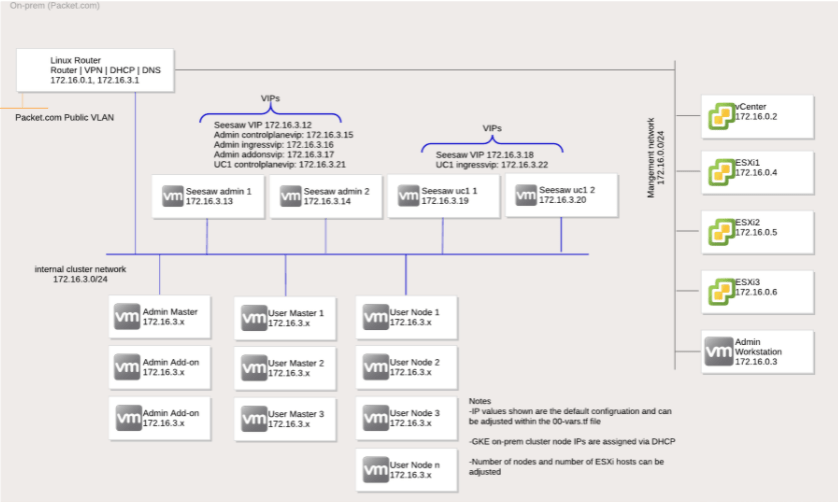
我們先從架構說明開始吧!今天我們會跟各位分享較為簡易的架構,是跟Google所提供的高效開源SEESAW LB進行整合的架構,這樣的架構具備以下幾個優勢:
- 只需要一個Subnet,就可以完成所有的環境部署,與Anthos on Bare Metal的環境部署需求極為相似,也近似於開源K8S的部署環境。
- 內建開源SEESAW LB,作為ELB使用,提供L4 LB & Ingress的接入訪問存取
- Admin / User Cluster分離,可透過Admin Cluster來集中管理所有的User Cluster,提供管理、服務的資源分離,避免彼此互受影響。
軟體資源需求:
- VMware Enterprise Plus(with DRS feature) 6.7U3以上的版本 * 3
- vCenter Server 6.7U3以上的版本 * 1
最低虛擬化硬體資源需求 :
- 8 physical CPUs @ 2.7GHz with hyperthreading enabled
- 40 GiB RAM
- 450 GiB of storage
最低系統核心元件數量:
Load balancer:
- Seesaw / f5 load balancing * 1
admin cluster :
- Admin cluster control-plane node * 1
- admin cluster add-on nodes * 2
- user-cluster control-plane node * 1
User Cluster :
- worker nodes * 3
因為是高度與VMware進行整合的方案,因此在軟體授權、硬體資源的要求上會比一般的開源方案來的高些,初期可能會覺得成本略高,但如果對比平台系統的可靠度、後續的管理維運成本,就會發現這些投資是非常值得的!
軟體調整需求:
因為是透過自動下載VM Image的方式進行部署,所以並不需要特別進行調整!
VMware環境部署需求:
- 預先完成VMware ESXi部署安裝(6.7U3以上版本)
- 預先完成vCenter部署與安裝(6.7U3以上版本)
- 預先創建兩個resource group,後續透gkeadmin / gkectl創建資源時會用到:
- ANTHOS-ADMIN
- ANTHOS
VMware 網路部署需求:
因為是跟VMware平台進行整合,依據使用的vSwitch模式不同,會需要進行一些設置的微調,可以參考下列的說明來進行變更。
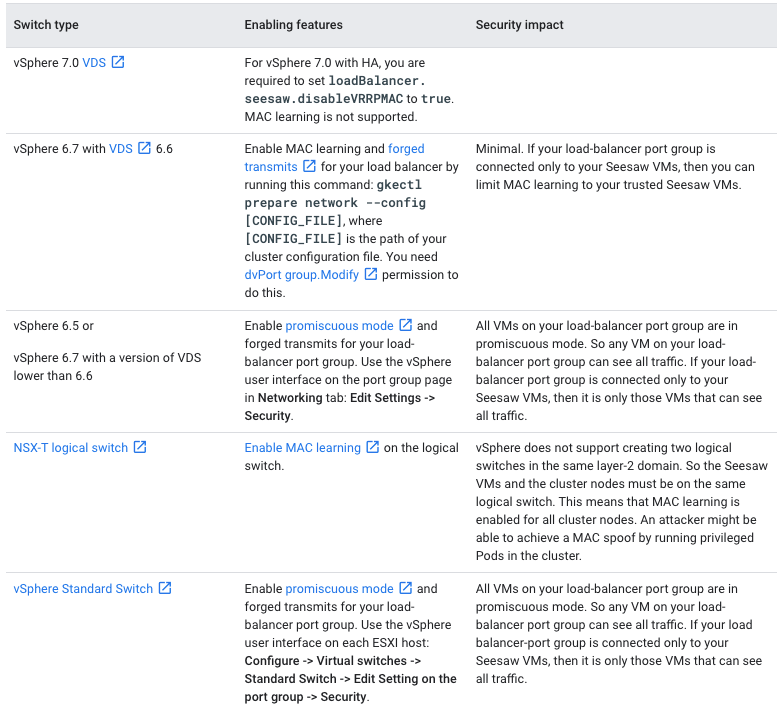
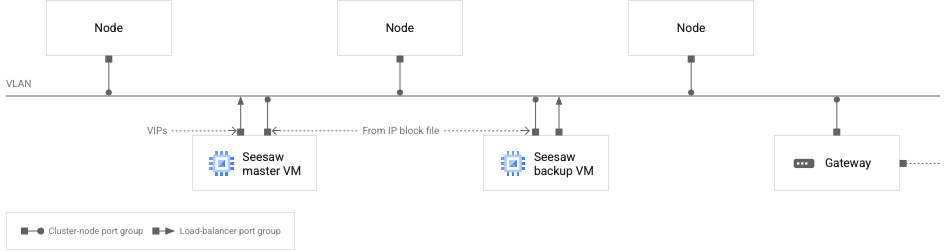
Anthos 提供免費的企業級SEESAW LB,藉由Direct Server Return(DSR)技術,提供高速的服務分流、轉發能力
Networking資源需求:
Anthos on VMware的網路架構非常的簡單,跟Anthos Bare Metal一樣,只需要一個subnet,搭配Bundled LB(SEESAW),就可以同時提供external L4 load balancing 還有master/worker的nodes網路存取,當然在許多的企業環境中,會希望拆分服務跟主機的網路區段,這部分當然也不是問題,只需要額外準備F5設備,透過Integrated的部署模式,就可以提供更進階的LB、資安防護功能(例如:WAF、機器人)等,當然,您也可以透過Manual模式與第三方的LB方案進行整合(例如:Citrix、VMware NSX-T firewall等…)
VMware vCenter權限需求:
因為是透過vCenter的API來進行自動化的環境部署,在大多數的企業環境中,並不會直接提供vCenter的最高管理權限給我們,因此可以先請目前的vCenter管理者,透過下列的GOVC指令,針對特定帳戶創建相應所需要的權限。
Note: 稍微留意一下紅色字的部分,替換成目前管理者的帳戶來進行執行,當設置完畢後,後續我們將採用藍色字的帳戶來進行Anthos on VMware的自動部署。
| export GOVC_USERNAME=ADMINISTRATOR_ACCOUNT@vsphere.local export GOVC_PASSWORD=ADMINISTRATOR_PASSWORD cat <<END |xargs govc role.create anthos Datastore.AllocateSpace Datastore.Browse Datastore.Config Datastore.DeleteFile Datastore.FileManagement Datastore.UpdateVirtualMachineFiles Datastore.UpdateVirtualMachineMetadata Folder.Create Folder.Delete Folder.Move Folder.Rename Host.Inventory.EditCluster InventoryService.Tagging.CreateTag Network.Assign Resource.ApplyRecommendation Resource.AssignVMToPool Resource.ColdMigrate Resource.HotMigrate Resource.QueryVMotion Sessions.ValidateSession StorageViews.View System.Anonymous System.Read System.View Task.Create Task.Update VApp.ApplicationConfig VApp.Import VApp.InstanceConfig VirtualMachine.Config.AddExistingDisk VirtualMachine.Config.AddNewDisk VirtualMachine.Config.AddRemoveDevice VirtualMachine.Config.AdvancedConfig VirtualMachine.Config.Annotation VirtualMachine.Config.CPUCount VirtualMachine.Config.ChangeTracking VirtualMachine.Config.DiskExtend VirtualMachine.Config.DiskLease VirtualMachine.Config.EditDevice VirtualMachine.Config.HostUSBDevice VirtualMachine.Config.ManagedBy VirtualMachine.Config.Memory VirtualMachine.Config.MksControl VirtualMachine.Config.QueryFTCompatibility VirtualMachine.Config.QueryUnownedFiles VirtualMachine.Config.RawDevice VirtualMachine.Config.ReloadFromPath VirtualMachine.Config.RemoveDisk VirtualMachine.Config.Rename VirtualMachine.Config.ResetGuestInfo VirtualMachine.Config.Resource VirtualMachine.Config.Settings VirtualMachine.Config.SwapPlacement VirtualMachine.Config.ToggleForkParent VirtualMachine.Config.UpgradeVirtualHardware VirtualMachine.GuestOperations.Execute VirtualMachine.GuestOperations.Modify VirtualMachine.GuestOperations.ModifyAliases VirtualMachine.GuestOperations.Query VirtualMachine.GuestOperations.QueryAliases VirtualMachine.Hbr.ConfigureReplication VirtualMachine.Hbr.MonitorReplication VirtualMachine.Hbr.ReplicaManagement VirtualMachine.Interact.AnswerQuestion VirtualMachine.Interact.Backup VirtualMachine.Interact.ConsoleInteract VirtualMachine.Interact.CreateScreenshot VirtualMachine.Interact.CreateSecondary VirtualMachine.Interact.DefragmentAllDisks VirtualMachine.Interact.DeviceConnection VirtualMachine.Interact.DisableSecondary VirtualMachine.Interact.DnD VirtualMachine.Interact.EnableSecondary VirtualMachine.Interact.GuestControl VirtualMachine.Interact.MakePrimary VirtualMachine.Interact.Pause VirtualMachine.Interact.PowerOff VirtualMachine.Interact.PowerOn VirtualMachine.Interact.PutUsbScanCodes VirtualMachine.Interact.Record VirtualMachine.Interact.Replay VirtualMachine.Interact.Reset VirtualMachine.Interact.SESparseMaintenance VirtualMachine.Interact.SetCDMedia VirtualMachine.Interact.SetFloppyMedia VirtualMachine.Interact.Suspend VirtualMachine.Interact.TerminateFaultTolerantVM VirtualMachine.Interact.ToolsInstall VirtualMachine.Interact.TurnOffFaultTolerance VirtualMachine.Inventory.Create VirtualMachine.Inventory.CreateFromExisting VirtualMachine.Inventory.Delete VirtualMachine.Inventory.Move VirtualMachine.Inventory.Register VirtualMachine.Inventory.Unregister VirtualMachine.Namespace.Event VirtualMachine.Namespace.EventNotify VirtualMachine.Namespace.Management VirtualMachine.Namespace.ModifyContent VirtualMachine.Namespace.Query VirtualMachine.Namespace.ReadContent VirtualMachine.Provisioning.Clone VirtualMachine.Provisioning.CloneTemplate VirtualMachine.Provisioning.CreateTemplateFromVM VirtualMachine.Provisioning.Customize VirtualMachine.Provisioning.DeployTemplate VirtualMachine.Provisioning.DiskRandomAccess VirtualMachine.Provisioning.DiskRandomRead VirtualMachine.Provisioning.FileRandomAccess VirtualMachine.Provisioning.GetVmFiles VirtualMachine.Provisioning.MarkAsTemplate VirtualMachine.Provisioning.MarkAsVM VirtualMachine.Provisioning.ModifyCustSpecs VirtualMachine.Provisioning.PromoteDisks VirtualMachine.Provisioning.PutVmFiles VirtualMachine.Provisioning.ReadCustSpecs VirtualMachine.State.CreateSnapshot VirtualMachine.State.RemoveSnapshot VirtualMachine.State.RenameSnapshot VirtualMachine.State.RevertToSnapshot END govc permissions.set -principal CLUSTER_USER_ACCOUNT@vsphere.local \ -role anthos -propagate=true |
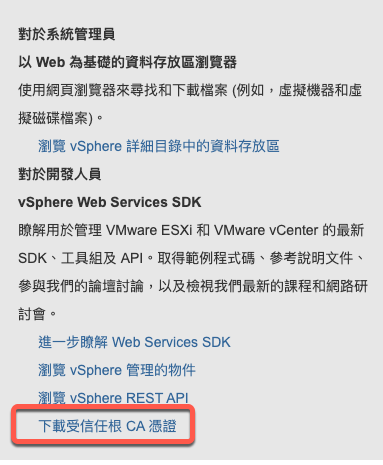
取得vCenter憑證檔案:
因為測試環境的vCenter是用自簽憑證,因此需要預先地將trust CA憑證下載下來(用瀏覽器,訪問VMware vcenter首頁就可以看到載點),並註記在後續的admini-ws-config.yaml設定檔中,這樣在部署的時候才不會發生錯誤。
GCP平台API需求:
新創建的GCP專案,需要啟動一些API服務,以利後續透過自動化部屬指令集,能夠順利地與其溝通。
Note: 稍微留意一下紅色字的部分,需替換成目前實際專案的PORJECT_ID
| gcloud auth login gcloud config set project PROJECT_ID gcloud services enable –project=PROJECT_ID \ anthos.googleapis.com \ anthosgke.googleapis.com \ anthosaudit.googleapis.com \ cloudresourcemanager.googleapis.com \ container.googleapis.com \ gkeconnect.googleapis.com \ gkehub.googleapis.com \ serviceusage.googleapis.com \ stackdriver.googleapis.com \ monitoring.googleapis.com \ logging.googleapis.com |
GCP平台相關設置需求:
在Anthos進行正式部署前,我們還需要先在GCP平台創建一個Service Account,用來協助我們進行後續的Service Account創建。
Note: 稍微留意一下紅色字的部分,需替換成目前實際專案的PORJECT_ID
| gcloud auth login gcloud config set project PROJECT_ID gcloud iam service-accounts create component-access-sa \ –display-name “Component Access Service Account” \ –project PROJECT_ID gcloud iam service-accounts keys create component-access-key.json \ –iam-account component-access-sa@[PROJECT_ID].iam.gserviceaccount.com gcloud projects add-iam-policy-binding PROJECT_ID \ –member “serviceAccount:component-access-sa@[PROJECT_ID].iam.gserviceaccount.com” \ –role “roles/serviceusage.serviceUsageViewer” gcloud projects add-iam-policy-binding PROJECT_ID \ –member “serviceAccount:component-access-sa@[PROJECT_ID].iam.gserviceaccount.com” \ –role “roles/iam.serviceAccountCreator” gcloud projects add-iam-policy-binding PROJECT_ID \ –member “serviceAccount:component-access-sa@[PROJECT_ID].iam.gserviceaccount.com” \ –role “roles/iam.roleViewer” |
管理工作站部署相關準備資料、說明:
Anthos 提供工作站、叢集部署工具(內建錯誤分析日誌),可幫助管理者大幅度簡化部署流程,並減少人為設置錯誤的發生機率
管理工作站部署:
Anthos on VMware的VM部署,是透過gkeadm指令集來進行部署的,您可以在下列連結中,取得該指令集。
https://cloud.google.com/anthos/clusters/docs/on-prem/1.8/downloads
當安裝完成指令集後,接下來就是要產生出設定檔範本並進行內容的修改,您可以透過下列指令來產生出範例設定檔。
| ./gkeadm create config |
當範例設定檔產生完畢後,接下來就是要進行內容的修改,可以參考小編提供的範例,另外稍微留意一下紅色字的部分,是需要依據實際的現況進行調整的。
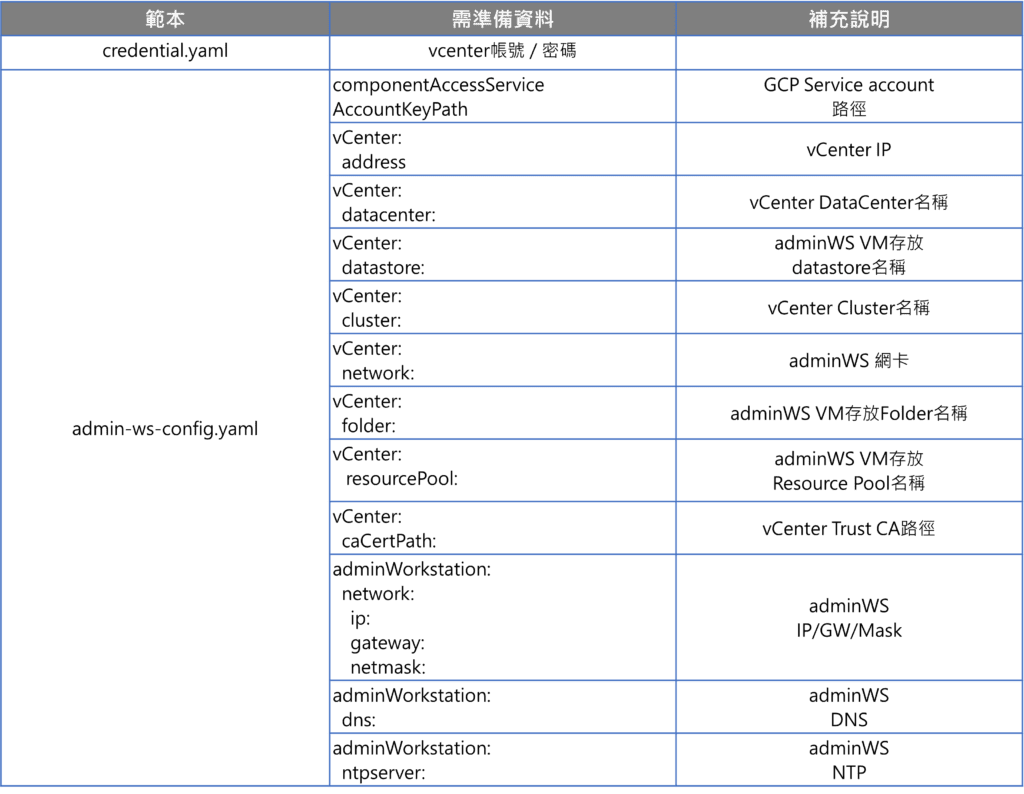
credential.yaml
| apiVersion: v1 kind: CredentialFile # list of credentials items: # reference name for this credential entry – name: vCenter username: “administrator@anthos-demo.local” password: “P@ssw0rd” |
admin-ws-config.yaml
| gcp: # Path of the component access service account’s JSON key file componentAccessServiceAccountKeyPath: “/Users/jamesitexpert/Dropbox/VSCode/GitHub/Anthos-VMWare-1.8.0/component-access-key.json” # Specify which vCenter resources to use vCenter: # The credentials and address GKE On-Prem should use to connect to vCenter credentials: address: “10.0.100.99“ # reference to vCenter credentials file fileRef: # read credentials from this file path: credential.yaml # entry in the credential file entry: vCenter datacenter: “ANTHOS-DEMO” datastore: “zerone-demo-esxi5” cluster: “DEMO” network: “MGMT” # vSphere vm folder to deploy vms into. defaults to datacenter top level folder folder: “ANTHOS” resourcePool: “ANTHOS-ADMIN” # Provide the path to vCenter CA certificate pub key for SSL verification caCertPath: “/Users/jamesitexpert/Dropbox/VSCode/GitHub/Anthos-VMWare-1.8.0/certs/lin/0950b59b.0“ # The URL of the proxy for the jump host proxyUrl: “” adminWorkstation: name: gke-admin-ws_1-8-0 cpus: 4 memoryMB: 8192 # The boot disk size of the admin workstation in GB. It is recommended to use a # disk with at least 50 GB to host images decompressed from the bundle. diskGB: 50 # Name for the persistent disk to be mounted to the home directory (ending in .vmdk). # Any directory in the supplied path must be created before deployment. dataDiskName: gke-on-prem-admin-workstation-data-disk/gke-admin-ws-210706-154134-data-disk.vmdk # The size of the data disk in MB. dataDiskMB: 512 network: # The IP allocation mode: ‘dhcp’ or ‘static’ ipAllocationMode: “static” # # The host config in static IP mode. Do not include if using DHCP hostConfig: # # The IPv4 static IP address for the admin workstation ip: “10.0.100.97“ # # The IP address of the default gateway of the subnet in which the admin workstation # # is to be created gateway: “10.0.100.254“ # # The subnet mask of the network where you want to create your admin workstation netmask: “255.255.255.0“ # # The list of DNS nameservers to be used by the admin workstation dns: – “8.8.8.8“ – “168.95.1.1“ # The URL of the proxy for the admin workstation proxyUrl: “” ntpServer: clock.via.net |
準備好了部署credential.yaml & admin-ws-config.yaml的部署腳本,接下來就是進行部署啦!
因為我們希望gkeadm指令,能夠在創建adminWS VM的同時幫我們創建好需要的service account,所以在部署的時候,記得要多加上一個 –auto-create-service-accounts的參數。
萬一在部署過程中發生錯誤,您可以從logs的目錄中,去確認相關的部署日誌,裡面有各階段的執行歷程,如果失敗了,只要針對該內容進行修正、調整,再進行一次部署就可以囉!
| ❯ ./gkeadm create admin-workstation –auto-create-service-accounts Using config file “admin-ws-config.yaml”… Running preflight validations… – Validation Category: Tools – [SUCCESS] gcloud – [SUCCESS] ssh – [SUCCESS] ssh-keygen – [SUCCESS] scp – Validation Category: Config Check – [SUCCESS] Config – Validation Category: SSH Key – [SUCCESS] SSH key path – Validation Category: Internet Access – [SUCCESS] Internet access to required domains – Validation Category: GCP Access – [SUCCESS] Read access to GKE on-prem GCS bucket – Validation Category: vCenter – [SUCCESS] Credentials – [SUCCESS] Version – [SUCCESS] Datacenter – [SUCCESS] Datastore – [SUCCESS] Resource Pool – [SUCCESS] Folder – [SUCCESS] Network – [SUCCESS] Datadisk All validation results were SUCCESS. Reusing VM template “gke-on-prem-admin-appliance-vsphere-1.7.2-gke.2” that already exists in vSphere. Creating admin workstation VM “gke-admin-ws-210622-083437″… – Creating admin workstation VM “gke-admin-ws-210622-083437″… DONE Waiting for admin workstation VM “gke-admin-ws-210622-083437” to be assigned an IP…. DONE ****************************************** Admin workstation VM successfully created: – Name: gke-admin-ws-210622-083437 – IP: 10.0.100.98 – SSH Key: /Users/jamesitexpert/.ssh/gke-admin-workstation ****************************************** Printing gkectl and docker versions on admin workstation… gkectl version gkectl 1.7.2-gke.2 (git-5b8ef94a3) Add –kubeconfig to get more version information. docker version Client: Version: 19.03.2 API version: 1.40 Go version: go1.12.9 Git commit: 6a30dfca03 Built: Tue Oct 13 16:38:16 2020 OS/Arch: linux/amd64 Experimental: false Server: Engine: Version: 19.03.2 API version: 1.40 (minimum version 1.12) Go version: go1.12.9 Git commit: 6a30dfca03 Built: Tue Oct 13 14:47:06 2020 OS/Arch: linux/amd64 Experimental: false containerd: Version: 1.4.3-0ubuntu0~18.04.1 GitCommit: runc: Version: spec: 1.0.1-dev GitCommit: docker-init: Version: 0.18.0 GitCommit: Checking NTP server on admin workstation… ntptime ntp_gettime() returns code 0 (OK) time e47d56f9.ad765774 Wed, Jun 23 2021 6:45:13.677, (.677587280), maximum error 13000 us, estimated error 0 us, TAI offset 0 ntp_adjtime() returns code 0 (OK) modes 0x0 (), offset 0.000 us, frequency 0.000 ppm, interval 1 s, maximum error 13000 us, estimated error 0 us, status 0x2000 (NANO), time constant 2, precision 0.001 us, tolerance 500 ppm, Getting component access service account… Enabling APIs… – project cmuh-anthos-prerequisite (for component-access-sa) – serviceusage.googleapis.com – iam.googleapis.com – cloudresourcemanager.googleapis.com Configuring IAM roles for service accounts… – component-access-sa for project cmuh-anthos-prerequisite – roles/serviceusage.serviceUsageViewer – roles/iam.serviceAccountCreator – roles/iam.roleViewer Preparing “credential.yaml” for gkectl… Copying files to admin workstation… – /Users/jamesitexpert/Dropbox/VSCode/GitHub/Anthos-VMWare/certs/lin/0950b59b.0 – /Users/jamesitexpert/Dropbox/VSCode/GitHub/Anthos-VMWare/component-access-key.json – /var/folders/s8/2sc278g92j3c69qr09p6_8sc0000gn/T/gke-on-prem-vcenter-credentials459302017/credential.yaml Preparing “admin-cluster.yaml” for gkectl… Preparing “user-cluster.yaml” for gkectl… ******************************************************************** Admin workstation is ready to use. WARNING: file already exists at “/Users/jamesitexpert/Dropbox/VSCode/GitHub/Anthos-VMWare/gke-admin-ws-210622-083437”. Overwriting. Admin workstation information saved to /Users/jamesitexpert/Dropbox/VSCode/GitHub/Anthos-VMWare/gke-admin-ws-210622-083437 This file is required for future upgrades SSH into the admin workstation with the following command: ssh -i /Users/jamesitexpert/.ssh/gke-admin-workstation ubuntu@10.0.100.96 |
當administrator workstation部署完畢後,我們就可以透過SSH + Key的方式登入到設備中,如果部署順利,應該會看到目錄中有產生三把service account key,以及admin-cluster、user-cluster的範本。
| ssh -i /Users/jamesitexpert/.ssh/gke-admin-workstation ubuntu@10.0.100.96 ls -1 admin-cluster.yaml connect-agent-sa-2106231753.json connect-register-sa-2106231753.json log-mon-sa-2106231753.json user-cluster.yaml 0950b59b.0 component-access-key.json |
今天的內容差不多到了Anthos on VMware(上篇)的尾聲啦!在這篇的內容中,我們跟各位介紹了何謂Anthos on VMware,以及相關部署所需要注意的內容、說明,同時也提供了一些部署時會用到的設置範本,讓各位在未來實際環境的部署時,能夠進行內容的對照、修正,加速各位的部署。
下篇我們將延續上篇的內容,帶各位進行Admin & User Cluster的部署,記得要持續關注我們,掌握最新的Anthos技術、實作分享!敬請期待,也歡迎大家關注我們的活動網頁、Line頻道,就可以在第一時間獲得我們的最新更新囉!
發佈日期: 2021-09-24 | James Wu
更多雲地混合解決方案 : 雲地混合規劃與建置
